Does your business need co-managed IT support?
by Jon Lober | NOC Technology
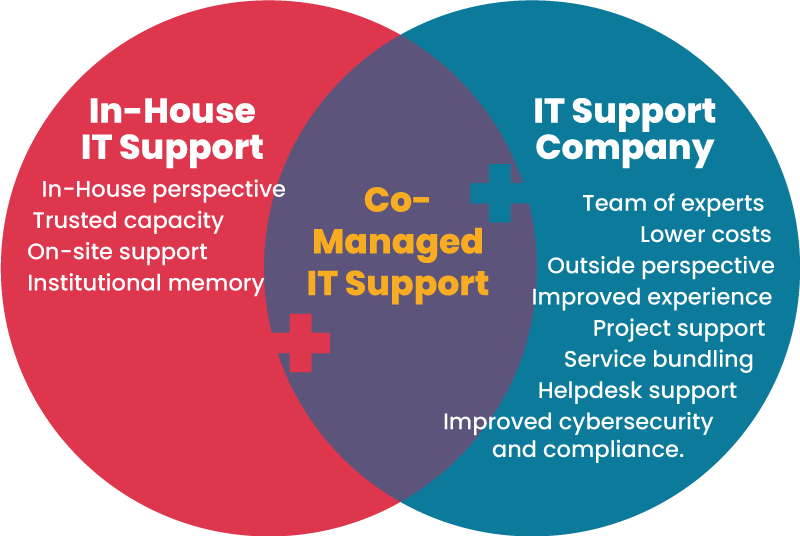
For many small businesses, co-managed IT support can offer the best of both worlds: internal staff and insight with access to a team of experts and overflow support. We previously examined eight benefits of a co-managed arrangement; this post will help decision-makers decide if co-managed IT support is the right model for their organization.
Three conditions are required for a successful IT co-management arrangement.
A successful IT co-management model requires three conditions:
- A small business that requires additional IT support capacity.
- Capable and trustworthy existing in-house IT support
- An IT service provider that can complement existing support more comprehensively and cost-effectively than a single additional employee.
Does this sound like you?
Book a meeting with one of our IT experts today.
When decision-makers recognize and agree with all three statements, co-managed IT support is often the most effective solution. However, if even one of these criteria is false, another course of action is recommended.
- If #1 is false. A business has no need for additional support.
- If #2 is false. A business should replace existing IT staff with other, more capable employees or a full-management contract with an MSP.
- If #3 is false. A business should hire an additional IT employee.
Four indicators that a business should actively seek co-managed IT support.
If a small business meets the three co-managed IT conditions above and agrees that co-managed support is their best option, the management team must then decide when to move forward. The following four indicators are ordered in importance from highest to lowest and can help decision-makers determine how quickly they should seek assistance. The indicators are ordered from highest priority to least concern though the presence of multiple indicators in a business suggests a greater degree of urgency.
1. Incomplete cybersecurity coverage.
Most technicians understand the importance of cybersecurity and a few of its basic tools, but precious few possess true expertise in the area. IT staff that underestimate the risk often inflict a terrible cost on their employer when an attack inevitably occurs. Those techs that recognize the extent of the challenge frequently feel hopeless about adequately addressing the ever-evolving threat without support.
The fifth annual (ISC)² Cybersecurity Workforce Study revealed an expanding gap between the capacity of the growing cybersecurity workforce and the severity of the cybercrime threat. This data supports our anecdotal evidence that even the few companies that proactively implement in-house cybersecurity measures are doing too little too late.
Cybersecurity coverage must be comprehensive in order to be effective. Partial cybersecurity is like a partially sealed submarine. Even the smallest leak can be deadly. Only robust frameworks like the multilayered model and zero-trust architecture provide reliable protection for businesses navigating the digital depths of modern commerce.
2. Overwhelmed IT staff.
Driven by desperation and exasperation in their daily tasks, perfectly competent IT employees are frequently turning to Google. Their search terms? IT help, IT installers, helpdesk support, network support, outsourced IT companies.
Once an IT department reaches this point, the stability, security, and efficiency of a business’s digital infrastructure is at risk. Tech support will fall behind for employees across the company. Unresolved problems will mount as IT staff assume the position of firefighters, prioritizing the most serious flames while others smolder out of sight. A series of IT emergencies or a backlog of unanswered service requests are red flags that a business’s tech system is at risk.
3. Uncertainty regarding digital compliance.
Digital compliance is a rapidly evolving landscape that exists well beyond the job description of the average IT technician. As international, federal, and state governments implement new laws regulating consumer privacy and data breach reporting, the burden of compliance for the average small business is steadily rising. By the end of 2024, the data of nearly 75% of the population will be protected by one or more privacy regulations. Businesses that fail to proactively implement the required legal safeguards are increasingly finding themselves the target of litigation.
4. Impending IT projects.
Unfortunately, IT hardware has a relatively short lifespan and the nature of modern business technology is constantly evolving. As a result, a significant IT project is usually just around the corner—if not being actively postponed due to budget and/or staffing constraints. Server upgrades, network maintenance, computer stock replacement, new office setup, SharePoint configurations: the list goes on and on. Due to limited resources, most small businesses employee only as many staff members as are absolutely necessary to cover their daily needs, leaving scant time available for such projects.
In addition to the limitations of time and finances, constraints in expertise may also exist in an IT project. While many routine projects are within the ability of in-house IT staff, others require specialized knowledge that may be beyond the scope of the average technician to implement. Cloud migrations, transitions to VoIP phone systems, security camera systems, cybersecurity implementation, database setup or migrations are all good examples.
Co-managed IT support and your small business.
If you think that your small business might benefit from co-managed IT support and would like some hard numbers to consider with your team, let us know. We serve a number of businesses throughout Missouri and around the country through co-managed IT support contracts and would be happy to talk through your options and provide you with some real numbers to consider and compare.
Even if you decide that NOC Technology is not the right fit for your company, we would still be happy to help you think through what services might bring you the greatest benefit and what a good partner might look like for your business. If you are actively seeking a fully-managed or co-managed IT service provider, check out our IT Services Buyer’s Guide. This PDF resource is full of IT support advice for management teams and questions they should ask prospective outsourced IT providers before making a final decision.







