Hiding in Plain Sight - Advanced Phishing Technique
by Jon Lober | NOC Technology
Phishing attacks are now using advanced methods to slip past common security measures and well-trained users. Learn what these methods are and how you can mitigate them.
Most of today’s most prevalent phishing attacks rely on social engineering—methods and tactics that hackers use to trick unsuspecting victims into revealing their sign in credentials or financial information.
Employees that attend regular training can usually learn to successfully recognize and avoid most of these scams.
However, a certain class of phishing attacks go beyond the basic suite of confidence tools and deception. Using html tricks, non-Latin alphabet characters, and an acute understanding of cybersecurity countermeasures, some scammers are able to produce phishing emails that are nearly undetectable.
By exploiting the minute gap between security software’s scans of text and the scrutiny of a trained user’s eyeballs, scammers are able to hide their most clever methods in plain sight.
Here’s how they do it.
1. Homograph and Homolyph Attacks
Some of us might catch www.PayPaI.com. Most of us would never miss www.g00gle.com. Yet, not all spoofed websites are so easy to catch. Can you spot the differences in the following?
1. A. www.PаyPal.com vs. B. www.PayPal.com
2. A. www.google.com vs. B. www.gοοgle.com
3. A. www.micrоsоft.com vs B. www.мicrosoft.com
In each of these examples, at least one option is spoofed.
By using characters from International Domain Names (IDNs), hackers can mislead even the most perceptive of eyes by using optically identical characters—known as homolyphs or homographs. Although not all browsers or email clients will display them as the same, these look-alikes display identically in many contexts—even when you hover your cursor over them.
In example number one, option A has a Cyrillic (eastern European alphabet) “а” instead of the common Latin character “a,” used by English speakers. Number two replaces the “o”s in Google in option B with Greek omicrons. Finally, though you might be able to see the Cyrillic “M” in option B, you might have missed the Cyrillic “o”s in option A.
Although our eyes see the same character, your computer does not. Clicks on any such compromised links can direct you to a spoofed website that can easily steal any information that you provide on the site.
Most browser search bars now show international characters in a different format known as punycode, which displays websites with international domain addresses as beginning with “xn--.” However, most email clients do not show the punycode address, even when mousing over the link. As a result, you will not see the punycode address until after you have clicked the link in an email and navigated to it in your browser.
2. Zero-Point Fonts
In order to filter out potentially dangerous communications, email security software searches incoming mail for suspicious text or images and then quarantines it away from your inbox. Such software reads all text to establish whether or not that message represents a threat.
Savvy hackers can confuse security software by mixing their message with invisible fonts. By literally setting parts of their message to a font size of zero, recipients can no longer see that portion of the text, but computers still can. This tactic allows them to reveal suspicious words and phrases only to the recipients. The software is usually none-the-wiser.
Email security software might typically flag or quarantine messages that contain some version of the phrase “Your Netflix account has been compromised.” Scammers can hide that message by adding in extra words in a zero-point font. The result of this method is that only the following bold words would be visible to you as the recipient, but entire paragraph is still visible to the security software.
We hope that you are enjoying Your Netflix account. Our quality has never been better. You have not compromised your commitment to top quality by choosing our service. Thank you for choosing us as your preferred streaming service.
Such a message can slip right past basic email security software, since the program detects nothing suspicious about the content. You would only see the bold words above and would receive no warning from your security software that the message could be malicious.
3. Procedurally-generated Graphics
Moves and countermoves define the cybersecurity game.
Security software can now often detect a counterfeit logo or misuse of an official logo. However, with some high-school level HTML coding, phishers can replicate simple logos, like Microsoft’s classic four-color logo, in ways that are very difficult for security software to detect.

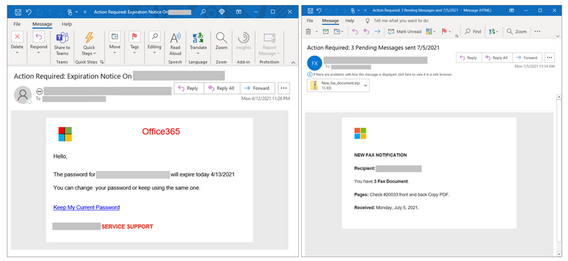
In an example published by Microsoft, hackers simply created a small HTML table and used a variety of color expression methods to fill in the table. By using a combination of color names, hex codes, and RGB values, security software was not able to recognize that the hackers were building a Microsoft logo using a variety of methods, though the optical result is immediately recognizable to a recipient.
4. Hidden Characters
By padding text with invisible characters, hackers can break up words and sentences to make them unrecognizable to security software. By inserting soft hyphens (that only appear when a word breaks at the end of a line) or a word joiner (a very fine amount of white space), scammers can “break apart” words in code that will still appear optically intact to the user.
Once again, an example might be helpful here. Can you spot the difference in the following words?
Dangerous vs. Dangerous
Although they appear optically identical, the second “Dangerous” has a word joiner (U+2060) inserted into the middle of it, rendering it as two separate words to security software -- Dan gerous. Though simplistic, this method, when implemented strategically, can be enough to confuse email scanning software—hiding the true intent from your security protocols, while leaving a dangerous trap in plain sight for the unsuspecting victim.
How can you protect yourself and your business from these advanced phishing techniques?
As you can see, these types of attacks are far more difficult to detect than a standard phishing scheme. The perpetrators behind these attempts pay close attention to detail and are unlikely to make as many typographic or design errors as those that recipients typically experience in more ordinary schemes.
So, how can you prevent falling prey to these sophisticated attacks?
1. Ongoing cybersecurity awareness training:
Quality awareness training is not a once-and-done event in cybersecurity, but a continual process. As trends emerge and wane, legitimate training programs will continuously keep you and your employees up-to-date on the latest threats and how to spot them.
2. Remain wary of all unsolicited or unfamiliar communication:
Your inbox is likely bombarded with advertisements, requests, and greetings. As a result of email fatigue, you might be more likely to drop your guard and just click through out of habit. If you receive any communication asking you to login or call that does not seem familiar—do not click or call! View any request to sign in to an account or call customer service with suspicion.
3. Threat detection using artificial intelligence (AI):
Human eyes and traditional security software can easily miss these optical and coding tricks. However, advanced threat detection like Microsoft Defender uses AI to learn how hackers are attacking inboxes right now. Such programs use what they learn across all inboxes in order to flag suspicious emails. Instead of ignoring a Cyrillic “a” or unusual Unicode characters, it will learn to associate them with phishing attempts and can protect users from reading such emails without any warning.
4. Do not click sign-in links from texts or emails:
This bears repeating. Even if you hover over a link and it appears legitimate, some of these advanced phishing techniques can still manage to conceal a spoofed web domain. Although you may recognize the service that requests you to sign in; you are sure that you have an account with them; and the stated concern seems legitimate—do not click the link or call the number. Instead navigate to that company’s website through your browser and sign in through their main page or call the number listed on their website.
5. Contract a multi-service provider (MSP) to help you maintain adequate cybersecurity:
Beyond these methods, high-quality MSPs can provide additional layers of advanced technological solutions, strategies, human oversight, and training to help you maintain the right balance of cybersecurity for your business. Enough to keep you safe without bogging you down with a burdensome amount of tech.





