Password Security
by Jon Lober | NOC Technology
Old and new recommendations for keeping your digital assets secure.

In honor of World Password Day, we’re going to review some longstanding best password practices and update you on some surprising recent recommendations that can help you improve password usage in your small business.
Why do we need to go over password security again?
Because it’s still a major problem. 81% of company data breaches are due to poor passwords. Any guess on what the most popular password (still) is? password.
Password integrity remains a critically-important issue for businesses of all sizes despite significant improvements in modern cybersecurity resources such as two-factor authentication (2FA), password policies, and even the movement to eliminate passwords entirely.
Does any of the following look familiar to you?
- password1
- guest
- trustno1
- letmein
- qwertyuiop
- peanut
- blessed
- poohbear
Hopefully you don’t use any of these passwords or their closely-related cousins. The selection above was pulled from NordPass’s annual roundup of the world’s most popular passwords. These passwords were all in the United States’ top 200 list and represent easy pickings for any hacker.
Best password practices—some reminders
According to security.org, at the very least your business should implement the following characteristics to your organization’s passwords to ensure their integrity:
- Uniqueness: Each account should have an individual password not used in any other software or system. 52% of Americans use the same password across multiple accounts, leaving an open door to multiple accounts if hackers can breach just one.
- Strength: Longer and more complex passwords are stronger passwords. A mixture of uppercase and lowercase letters, numbers, symbols and even emojis (when permitted) make a password more complex. Do you want to see how strong your password is? Try this password strength tool.
- Storage: Don’t write your password down, rely on your memory, or share them with others. Password managers offer the most secure storage method for your suite of secrets.
- Authentication: Two-factor authentication (2FA) offers a far greater level of security than standard passwords. Add 2FA to your accounts to verify your identify through a dedicated app, SMS text, or email.
- Monitoring: Quality password managers will notify you if you have been compromised through a data breach behind the scenes of one of your accounts. Additionally, a good IT company with cybersecurity experience can help you perform dark web scans to make sure that no one is selling your information on the black market.
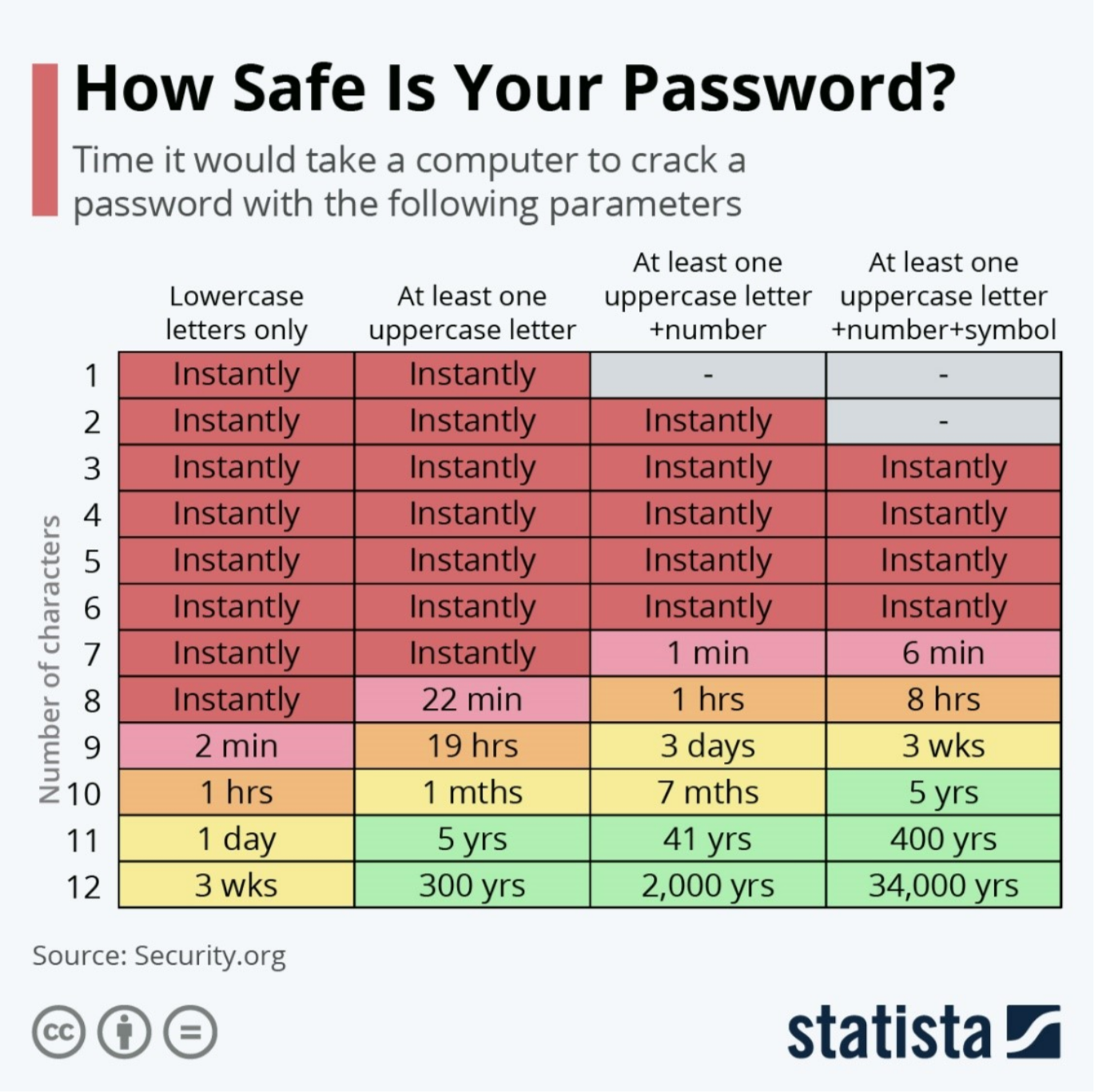
Prioritize longer passwords. Password length is more important than password complexity.
Although both length and complexity improve password effectiveness, length is a more effective factor according to the National Institute of Standards and Technology (NIST), the government body responsible for establishing best practices in cybersecurity.
In Special Publication 800-63B, the NIST’s most recent set of technical recommendations, the organization recognizes that strings of incomprehensible gibberish are difficult for the average human to memorize – and can lead to poor practices like password repetition. As a result, the NIST recommends that users prioritize longer, more memorable passwords or complex passphrases (a combination of words and symbols like Stay!oUt_0fH3re).
Artificial Intelligence (AI) commonly available to hackers can now crack even complex passwords with seven characters or less in under 6 minutes. As a result, a secure password should be at least 10 complex characters in length – with 12+ characters providing very secure results.
Don’t require periodic password updates.
Once again, human nature is behind this recent recommendation change from the NIST.
Although most IT professionals and cybersecurity experts previously recommended regular changes to your passwords, we now recognize that these requirements often lead to poor security habits. Instead of completely resetting a password to another unique strong password, users often just slightly adjust their current password or reuse a password from another account—compromising multiple systems.
Eliminate hints or other types of knowledge-based-authentication.
Instead of choosing complex questions and subtle answers for password hints or prompts, users tend to gravitate towards simpler, less forgettable possibilities. This makes it far easier for a potential cybercriminal to hack accounts. Since two-factor authentication offers a much more secure option for organizations, they should use this option instead of knowledge-based forms of authentication.