Phishing As A Service
by Jon Lober | NOC Technology
The prevelance and sophistication of phishing has reached a sobering new level.
The disaster-prone Nigerian prince and his schemes retired long ago. If you still classify phishing as a poorly-worded email that attempts to guilt you into sending money through Western Union, you need to get yourself up to date on the reality of today’s phishing environment.
Although some of today’s phishing scams are still poorly executed and painfully obvious, the most dangerous ones arise from sophisticated operations that can be extremely difficult to detect.
Today’s most serious widespread phishing threats originate from hacking organizations that offer phishing-as-a-service or “PaaS.” These groups offer sets of phishing tools or services to anyone who wants to purchase them or execute an attack on a specific victim.
Many of these groups operate with impunity. They run their websites on the clear web, set up user accounts, offer discounts, and post YouTube videos of their services and offerings. With their target market, their niche offerings, and marketing budget, they attract hackers with an appealing set of services that can facilitate large-scale phishing attacks.
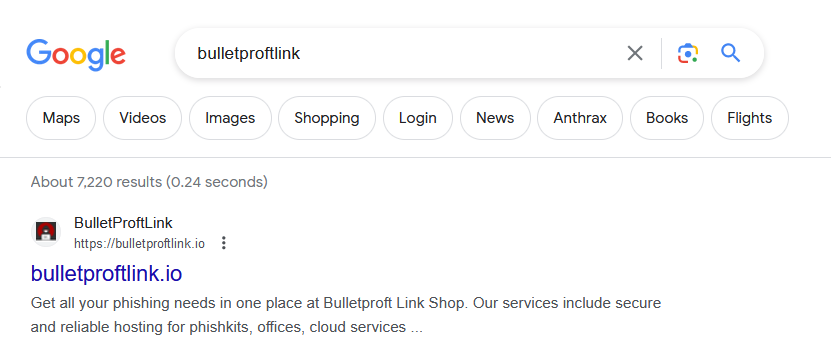
In this article, we will look at two prevalent PaaS schemes, Greatness and Bullet Proof Link (also known as BulletProftLink or Anthrax), which have provoked recent warnings from Microsoft and Cisco.
What is Bullet Proof Link?
Most likely based in Russia or Malaysia, this phishing group has been well known to cybersecurity groups for several years. Particularly brazen, even for a PaaS group, Bullet Proof Link maintains a website in the clear web (as shown in the Google search above) that directs users to a run-of-the-mill sign-in page that even allows clients to sign in with their Google account.

The group offers phishing kits and services, which consist of proxy IP addresses and domains, email templates, phishing sign-in pages, cloud storage, services hosting, and more. Anyone that wants to start a phishing operation can simply pay for Bullet Proof Link’s services and then begin a phishing campaign against whatever target they choose.
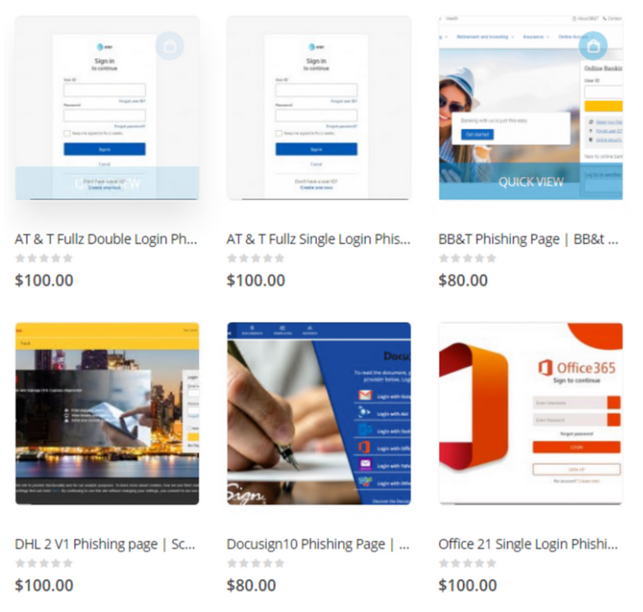
Over the past year, Microsoft’s security team has observed increasing complexity in the group’s attack methods. Cybersecurity professionals often use “impossible travel” alerts to flag a hacker that is using a VPN to virtually jump around the globe while executing an attack. For example, an infiltration starting from Madrid and then switching to Tokyo four hours later is physically impossible—alerting software to an impossible scenario that may indicate the presence of a hacker.
In order to avoid such an alert, Bullet Proof Link now uses residential IP proxies to set-up virtual shop in the same geographic vicinity of the target, limiting the amount of scrutiny that they might receive.New Paragraph
What is Greatness?
Fairly new to the phishing scene, Greatness is a very polished PaaS scheme that was first noticed by the cybersecurity community in 2022. Unlike Bullet Proof Link, with its wide range of potential victims, Greatness has a very narrow focus—Microsoft business clients. Using a specialized set of tools and techniques, the hacking group allows its clients to directly target businesses using Microsoft’s 365.
When successful, Greatness’s modus operandi allows its clients to steal credentials and access internal business networks in one swipe. Cisco’s elite Talos Intelligence Group recently issued an alert and overview of the Greatness attack protocol, and the details are alarming.
A Greatness attack typically begins through what appears to be a legitimate email from a coworker. Inside the email is a decoy HTML attachment charading as a shared document. When users click the file, the browser displays a blurred document screen that seems to have a hard time loading the document. When the document fails to load, the user is directed to a mirrored Microsoft 365 login screen with the appropriate Microsoft and/or company logos.
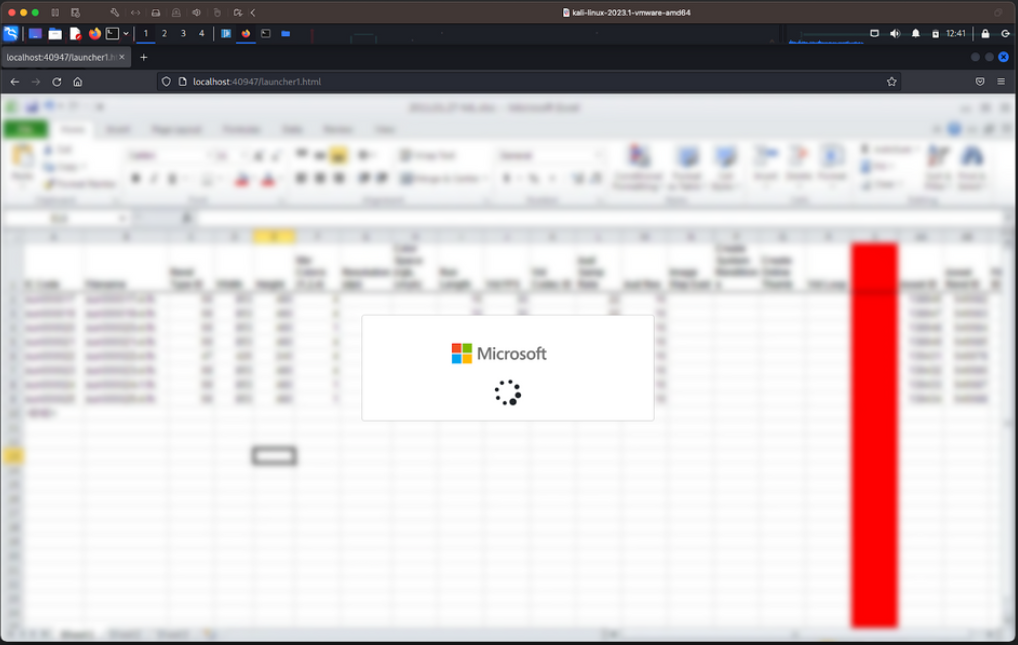
Once the user enters their information, Greatness signs into Microsoft 365 with the victim’s credentials. If prompted for multi-factor authentication (MFA), the service’s mirrored sign in screen will then prompt the user for the appropriate code sent to their phone, email, or authenticator app. At that point, if the user enters the code, the Greatness hacking client will have full access to the victim’s Microsoft 365 account and data.
How to protect yourself and your business against Greatness, Bullet Proof Link, and other PaaS attacks.
A good suite of cybersecurity tools can dramatically reduce your risk of exposure. Advanced firewalls, secure internet gateways, endpoint security, and AI email security all work in tandem to prevent this type of attack from succeeding by blocking the original email, stopping you from downloading the malicious file, preventing you from accessing a compromised domain, or quarantining an attack vector.
However, even the most advanced cybersecurity setup may not completely eliminate your exposure to such sophisticated phishing. The last and best line of defense will always be the user with the mouse. Once they click the suspicious link and enter their credentials, the attack has succeeded. Any cybersecurity system is incomplete without training that user to stop prior to entering their information.
Any attack that makes it past your digital defense will need to be stopped by wary employees. Cybersecurity training can help employees automatically recognize red flags in the email or compromised login process. Ongoing testing and benevolent hacking or phishing attempts by a cybersecurity professional can keep employees on their toes by simulating attacks from time to time. As the training progresses, employees can learn to automatically check for suspicious activity and prevent successful attacks.
If you are not sure what tools and training might work best for your organization to defend itself against PaaS attacks, look for a qualified MSP that can provide cybersecurity advice, strategy, or oversight. The investment will be well worth it.





