Phishing Report: QR Code Phishing a.k.a Quishing
by Jon Lober | NOC Technology
What should do you do with a suspicious QR code?
Over time, fish learn to avoid common artificial lures. If a fisherman continues to use the same bait in the same hole season after season, the fish get wise and stop taking the bait. As a result, dedicated fishing enthusiasts never stop seeking the perfect bait. Every year, new lures trickle into their tackle boxes, each with an innovation designed to convince a wary fish to bite.

As it turns out, anglers seeking Pisces in ponds are not the only ones that understand this principal. Phishers and scammers are constantly tweaking their methods and lures in ways that could convince savvy users to click. Every now and then, they invent a completely new category of bait. Today we are going to take a look at one of those examples
If you need a refresher on phishing—what it is and why it matters—read our first Phishing Report before you continue.
QR Code Scams: An Overview of “Quishing”
QR Codes (short for “Quick Response Codes”), have become nearly ubiquitous shortcuts into the virtual world. These black and white 2D patterns can encode up to 4,296 alphanumeric characters, which can be used to store serial numbers, passwords, URLs, email addresses, and more. Although they were invented nearly 30 years ago, QR codes only rose to their current popularity when smart phones took up residence in every pocket and purse.
Since QR codes can send users to virtually any website, they should be regarded with the same level of suspicion as any other link. Microsoft recently reported that scammers have been taking advantage of our familiarity with QR codes in a variety of contexts.
- Payment codes: When contactless methods became the de facto forms of payment during the height of the pandemic, QR codes became especially popular as a recognizable link to a payment site. However, clever scammers have been known to replace payment QR codes with spoofed payment sites. For example, linking from a parking meter to a lookalike parking authority website where payment details can be stolen.
- Package scams: Some clever scammers have been sending packages to residents with a QR code inside that purports to link them to return instructions. If you are ever linked by such a code to a website requesting payment information, close the webpage and report the scam to authorities.
- Donation scams: Unfortunately, nothing is sacred to most scammers. Flyers for impersonated nonprofits have been reported as using QR codes that link potential donors to spoofed websites requesting payment information.
- “Quishing” email scams: Like other phishing methods, QR phishing or “quishing,” impersonates an email from a recognizable or trustworthy company. The QR code provided in the email will ostensibly take the user to a site requesting payment information for a purchase that “did not go through.” In reality the victim is just giving away their credit card information to a scammer.
QR Code Phishing Attacks in the Workplace
A fellow managed service provider (MSP) recently alerted us to a new quishing attack that we consider to be particularly dangerous for businesses of any size. The phishing email posed as an internal email requesting the user to release “Held” messages by scanning a QR code.
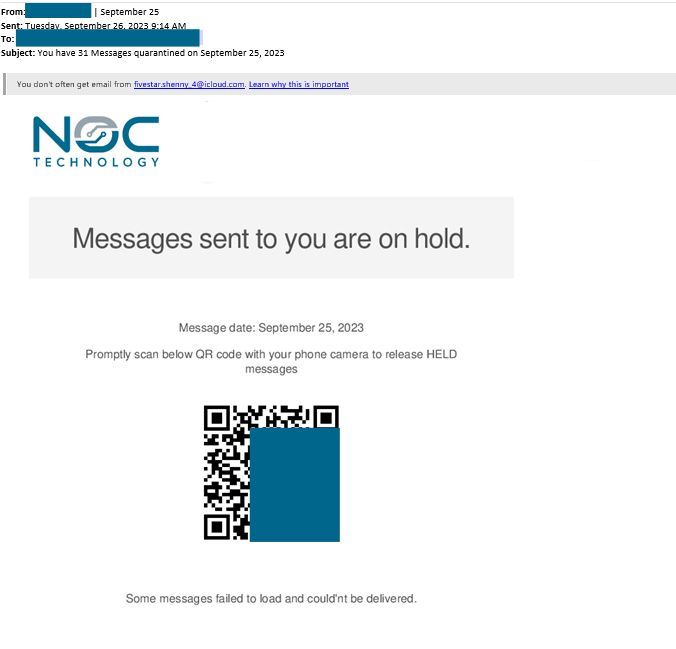
Unprepared users could easily scan the QR code, sign in, and continue on with their day without realizing that they had just given away the login information to their business accounts. Successful scammers could fool their victims into giving them access to an entire business network without anyone being the wiser.
The Lure: How this Phishing Method Works
Unlike our Geek Squad, PayPal, and Dicks Sporting Goods phishing analyses, this quishing attack is directly targeted at business users. This attack is refined, uses some very effective social engineering methods, and is likely causing significant damage to a number of businesses.
- Use of Company Logo: Many phishing attacks rely on trustworthy and recognizable logos to engender trust. This one goes uses the victim’s very own company logo in the company inbox to reduce the suspicion of the target user.
- Use of QR Code: In today’s digital environment, QR codes can apply a tech-savvy veneer to otherwise mundane communications. Though a user might never click a link in the same email, the appearance of a QR code shifts attention away from the link concealed in the black-and-white box to the belief that some tech system or individual sent a reliable communication.
- Simplicity: This email does not oversell nor undersell itself. Its language and formatting direct the user towards action without being flashy, ostentatious, or pushy. Excessive verbosity or imperative language would sound the alarm for informed users. The singular use of the word “promptly” is the only light application of urgency. The email’s design matches what most users would expect from an automated security system, right down to the QR code that dominates the middle of the message.
- Use of details: From the subject line to the QR code, this email suggests that it is a personal communication intended only for the targeted user. The subject line reads that there are “31” emails waiting on a specific date (September 25), which is repeated in the message body. The very QR code itself also implies that it is a personalized sign-in link.
- Appropriate use of vocabulary and grammar: “Quarantined,” “held,” “messages,” and “failed to load,” are all subtle uses of technical terms that are now a part of popular cybersecurity parlance. These words and (mostly) correct grammar all add to the illusion of validity.
Red Flags: How to recognize this scam
This is a well-executed attack, but it is not perfect. It contains several errors and tip-offs that should still alert a well-trained user.
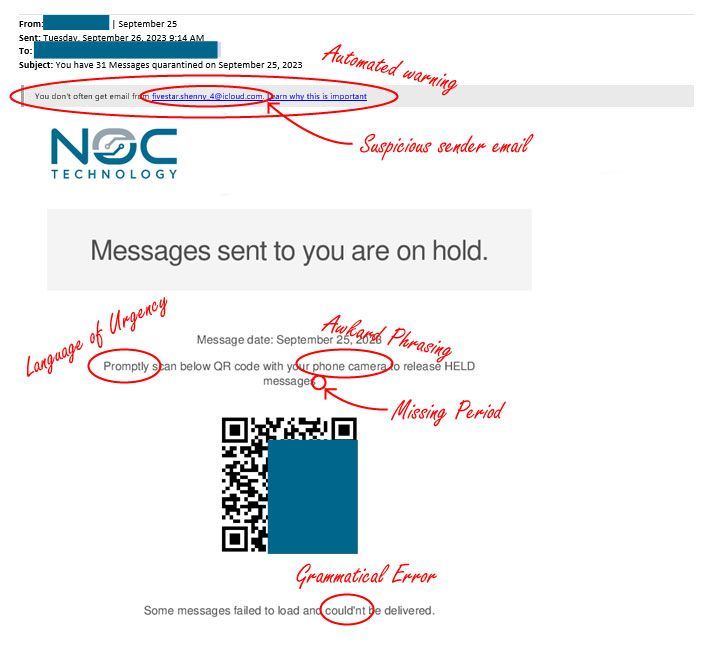
- Grammatical Errors: The classic phishing red flag is not absent from this email. Close attention reveals a misplaced apostrophe and missing period. In addition, contractions are unusual in this type of professional correspondence.
- Language of Urgency: Although the pressure is exceedingly light, the word “promptly” is still pushing the user towards unthinking, reflexive action and seems unnecessary in such a communication.
- Awkward Phrasing: The term “phone camera” is a bit awkward and non-standard. Any such phrases should trigger suspicion in wary users.
- Warning banner: Although many users begin to ignore such banners, they exist for a reason. These banners alert users that all may not be as it seems. Always read the banner, look at the email address, and consider if the communication is something that you are expecting.
- Unusual sender: This is the final piece to the puzzle warning a user not to click. No professional security system will be using fivestar_shenny_4@icloud.com as an email address. No matter what sender appears as in the “sender” line, always, always, always check the originator’s email address.
What should you do if you encounter a QR phishing email?
The warning signs above should be enough to warn you to not scan the QR code. If you do happen to scan the code, ensure that the link does not download anything to your PC. If you are taken to a page requesting personal or payment information, leave the page immediately.
If you encounter an email like our example above, take the following steps.
- Report the email to the FTC.
- Forward the email to your IT security team with a note describing your concerns.
- Report the email as phishing to your email provider. Major email providers usually have an option to “report as phishing.”
- Delete the email. You do not want you or your colleagues to accidentally scan the link at a later date.
- If you do scan a QR code like the one in the email above, immediately contact your IT cybersecurity team or a trustworthy MSP and let them know what happened.
If you would like more information on how to report a phishing email or what to do if you clicked, called, or scanned something suspicious, read our "How to report phishing emails" blog post for more comprehensive instructions.
Do you need help protecting your small business from digital threats?
If you do not know where to start, we want to help. We offer free, no-commitment, one-time consultations with our SMB tech experts to small business owners and IT personnel. Just let us know what your concerns are, and we can explain some of your options. Even if you just want to run an idea by us, we are here to help. Just click the button below to schedule a slot in our team's calendar.







