Multilayered cybersecurity: what is it, and do I need it?
by Jon Lober | NOC Technology
Learn the three layers of cybersecurity you need to protect your business from cyberattack.
Once upon a time, in a faraway land, there lived a successful duke. He had been his father’s youngest son, receiving only a meager portion of the family inheritance, yet he passed his days comfortably in a modest castle on a tidy estate. He was an industrious manager, faithfully reviewing his expenses and making shrewd investment.
Through perseverance and insight, he steadily acquired new parcels of land along his borders and increased his profits across his properties.
On occasion, the duke would visit eminent family members at their own castles where he witnessed intensifying countermeasures employed against thief and attack. Drawbridges were suspended over new moats. Walls were fortified and heightened. Guards were given new armor, trained to spot possible threats, and distributed throughout the interior of the castle. The family wealth was no longer on display in the great halls, but had been moved deep into a locked vault in the innermost dungeon; only trusted few with both password and key were permitted to enter.
Although the duke was steadfast, far-sighted, and determined, he consistently misjudged the true value of his holdings. Since his castle was smaller, his estate less resplendent than those of his elder brothers, he presumed his wealth to be insignificant. As he slowly increased his property and prosperity, he failed to escalate his security in commensurate measure—believing that such fortifications were unnecessary for his trivial treasures.
However, in the eyes of local bandits, the duke’s ever-growing riches were impossible to ignore. The gang knew that they were ill-equipped to tackle secure strongholds with multiple layers of defense. Only an equally-resourced foe could successfully penetrate the treasury behind those walls. However, the duke’s poorly-protected coffers could be accessed with only a little cunning and quick feet.
And so, the good duke was robbed of his hard-earned gold and reputation. Over many tireless decades, his persevering spirit had earned him renown and resources; yet sadly, his simple failure to properly safeguard them lost him both overnight.
Do not underestimate the value of your organization’s data.
Just like our duke, many SMB managers mistakenly believe that no one would bother to steal their business’s relatively limited amounts of client, vendor, and business data. Unfortunately for them, cybercriminals have learned that small businesses across the country are low-hanging fruit—with some surprisingly juicy pickings. The result? A full 43% of all cyberattacks are now aimed at SMEs.
In the modern business environment, every SMB will experience some form of cyberattack, yet only 14% are prepared to defend themselves according to the U.S. Small Business Administration (SBA). As a consequence, a single successful strike will close the doors of more than half of impacted small businesses.
Cybercrime inflicts damage on SMBs in a variety of ways.
- Direct theft of funds.
- Compensation costs to affected vendors or clients.
- Investigation and remediation costs.
- Business downtime.
- Loss of reputation in the marketplace leading to fewer customers.
That damage is imposed on businesses through an assortment of cybercrime tactics.
- Ransomware attacks lock away your data in exchange for a ransom.
- Phishing and smishing abuse human fallibility to gain access to sensitive information.
- Botnets silently control legions of infected computers.
- Business email compromise (BEC) attacks wreak havoc with private data and bank accounts by hijacking a legitimate organizational email account.
This list of threats names only a few of the most prevalent attack vectors; the FBI currently recognizes at least 26 distinct types of cybercrime. This high diversity of risks means that no single cybersecurity tool can effectively combat all possible digital threats faced by a modern business.
Protect your business with a multilayered cybersecurity approach.
Just like the barons and duchesses of old, today’s business managers must learn to effectively combat a wide variety of threats with an equally diverse set of defenses. We think of this comprehensive approach in terms of security layers—from the exposed periphery, through the vulnerable interior, to the vital core. Each level represents an opportunity to stop an intruder from accessing the critical data contained at the heart of a business and should be designed and implemented with the same care that managers apply to business bank accounts.
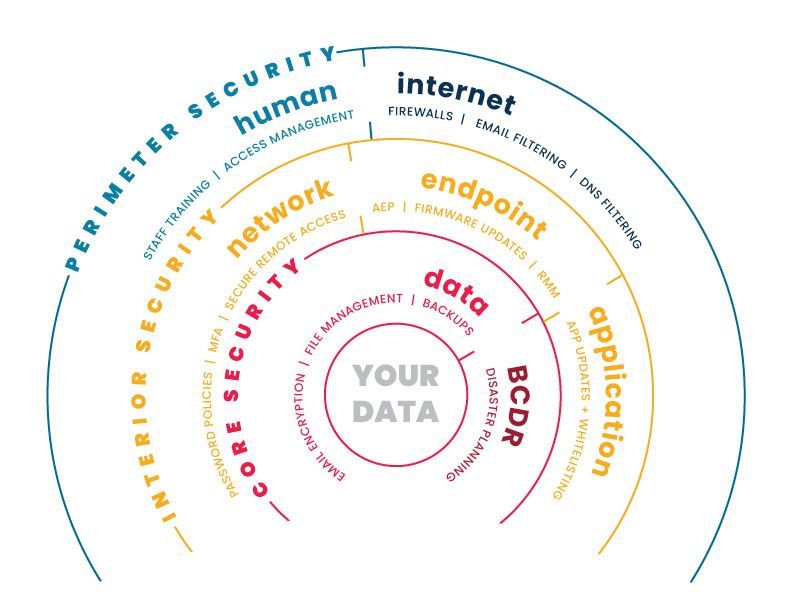
1. Perimeter Security
As the outermost layer of any security system, the perimeter should be designed to stop the vast majority of threats. In our stronghold analogy, the perimeter layer of cybersecurity represents the exterior of a castle: the moat, drawbridge, strong walls, sentries, and watchtowers. These defenses detect and deflect adversaries before they enter the stronghold. Threats that can be kept outside of the walls have been effectively mitigated and represent no material risk to resources inside of the castle.
The perimeter security of a modern business is composed human security and internet security practices. Internet security tools like firewalls and DNS filtering guard against threats originating in the public domain. Human security methods address the most vulnerable element of any cybersecurity setup—the people opening emails and initiating wire transfers. Password and IT policies, MFA, access management, and staff education are a few ways that we strengthen this most fallible area of a business.
2. Interior Security
Once an enemy infiltrates the castle wall, whether through brute force or deception, they must be automatically treated as a serious threat. Well-trained and trustworthy guards are the linchpin of this stage of defense. They must know who is allowed where and how to monitor attempts to penetrate valuable sections of the castle.
A managed service provider (MSP) like NOC provides interior security to a business by applying network, endpoint, and application security measures. Firmware is kept up to date. Advanced endpoint protections limit access to only users with valid permissions. 24/7 remote monitoring by cybersecurity professionals provide an immediate response to any alarms, and whitelisting ensures that only safe, up-to-date programs can be installed on company devices.
3. Core Security
Deep under the castle lays the treasury. Once a threat arrives to the stone-faced guard and steel door that protect the gold, they must present both password and key in order to achieve their goal. Should the worst occur and an enemy were to access the treasury, the security team should know exactly which gates to close and what steps to take to minimize the damage.
In any business, core security begins by limiting access to sensitive information to individuals who genuinely need access. Businesses must continually review permissions and update them accordingly. Email encryption should always protect sensitive information outside of restricted areas from unauthorized access.
Finally, even businesses that do everything right still sometimes fall prey to a well-planned attack—usually due to human error. As a result, every business should implement a comprehensive 3-2-1 backup plan, as well as a BCDR plan that includes first response, employee roles in a crisis, and cybersecurity insurance.
No one hopes for a house fire, but most of us make an evacuation plan and purchase fire insurance. Considering the ever-growing threat of cyberattack, SME managers would be wise to the same for their organizations. A comprehensive, multi-layered cybersecurity solution provides the best ROI for most small businesses.
If you are ready to start protecting your business data, reach out to our team of experts to learn how you we can help you implement a multilayered cybersecurity plan for your business.








