DocuSign Scam: What is it and what should you do?
by Jon Lober | NOC Technology
A fresh look at the DocuSign phishing scam
For several years, scammers have been leveraging the growing popularity and convenience of online e-signature and contract platforms for their own illicit gains. Not surprisingly, the list of spoofed companies includes the most widely-used of them all—DocuSign. These fraudulent emails are particularly dangerous since many victims are already accustomed to trusting the platform with personal information - including social security numbers and bank routing numbers.
Here at NOC Technology, we continue to see variations on this phishing scheme. Take a look at an example of a DocuSign email phishing attack we received, how to identify a DocuSign scam, and how to report a DocuSign scam email appropriately.
DocuSign Phishing Email Example
Several NOC Technology users received an email from “DocuShared ® Review” with the subject line: “Action required: DocuShared ® to NOC email address.” Upon opening the email, the recipients discovered (what appeared to be) a very standard DocuSign email, complete with DocuSign’s recognizable wordmark logo, blue envelope screen, and yellow “Review Document” button.
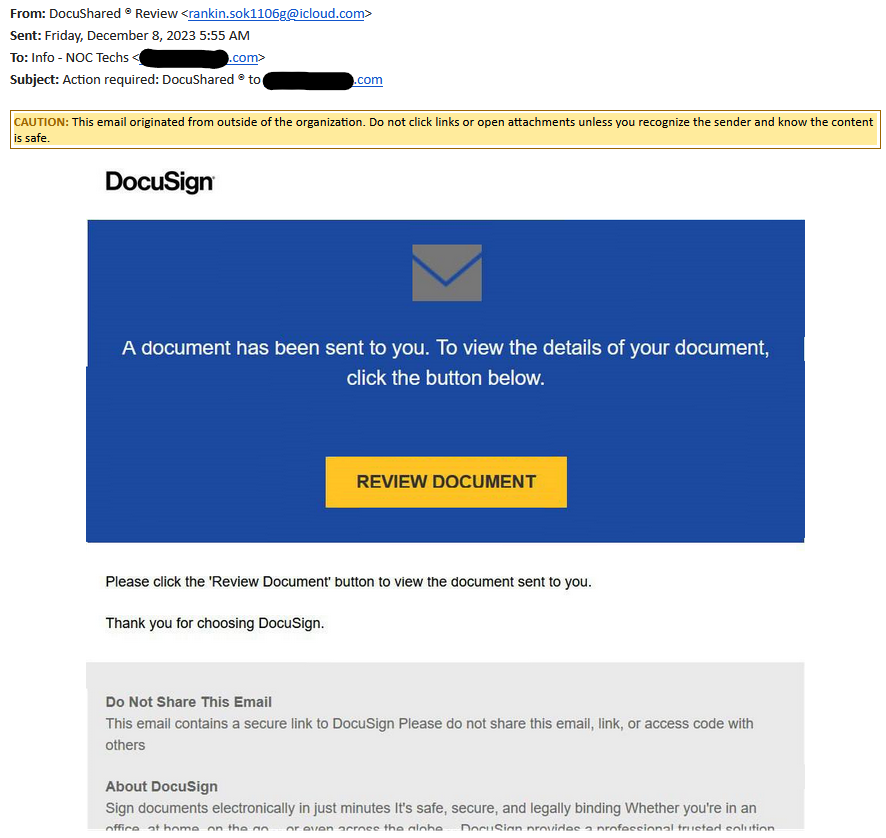
Phishing Lures: The Scammer’s Methods.
At first glance, everything about this email seems normal. For someone unthinkingly handling DocuSign documents on a daily basis, or someone waiting for a document, it would be all too easy to click.
- Direct inbox delivery: These scammers know what they're doing. Thanks to their understanding of spam filters, scammers are able to slide this type of message past email filters, dodge the spam box, and land it right next to the email from Brenda from HR. Behind the scenes, the plain text version of the email confounds security software, and the result is prime placement of tempting clickbait.
- Name and logo of a trusted company: The DocuSign name is synonymous with security and reliability. The cybercriminal's use of its name and logo plays directly to the potential victim’s inherent trust in these companies.
- Passive CTA: Your radar should go off if you see a high pressure call to action (act now or we'll permanently delete your account). But this insidious email does not directly ask the victim for anything suspicious, avoiding the internal alarms that go off when someone receives a pushy email asking for payment.
- Generic sender names and subject lines: Nothing to see here— and they're using that to their advantage. On the surface, everything about this email’s details seem like standard corporate communication.
- Use of the ® (Registered Trademark) symbol: Although the detail might seem insignificant, when combined with professional logos, layout, and colors, the air of legitimacy around this email begins to build.
- Incomplete message: Although this could simply be an error on the part of the scammer, or a tactic designed to avoid security measures (like we will see below), it could also be a genius move. The entire email is actually a clickable image that links the victim to the scammer’s landing page. Any attempts to click on the page to see the complete image could actually put the victim’s cybersecurity in real danger.
Red Flags: How to recognize a fake DocuSign email
Although this scammer has put some real effort into getting this message through to a target’s inbox, trained observers will quickly recognize several indications that the email is a fraud.
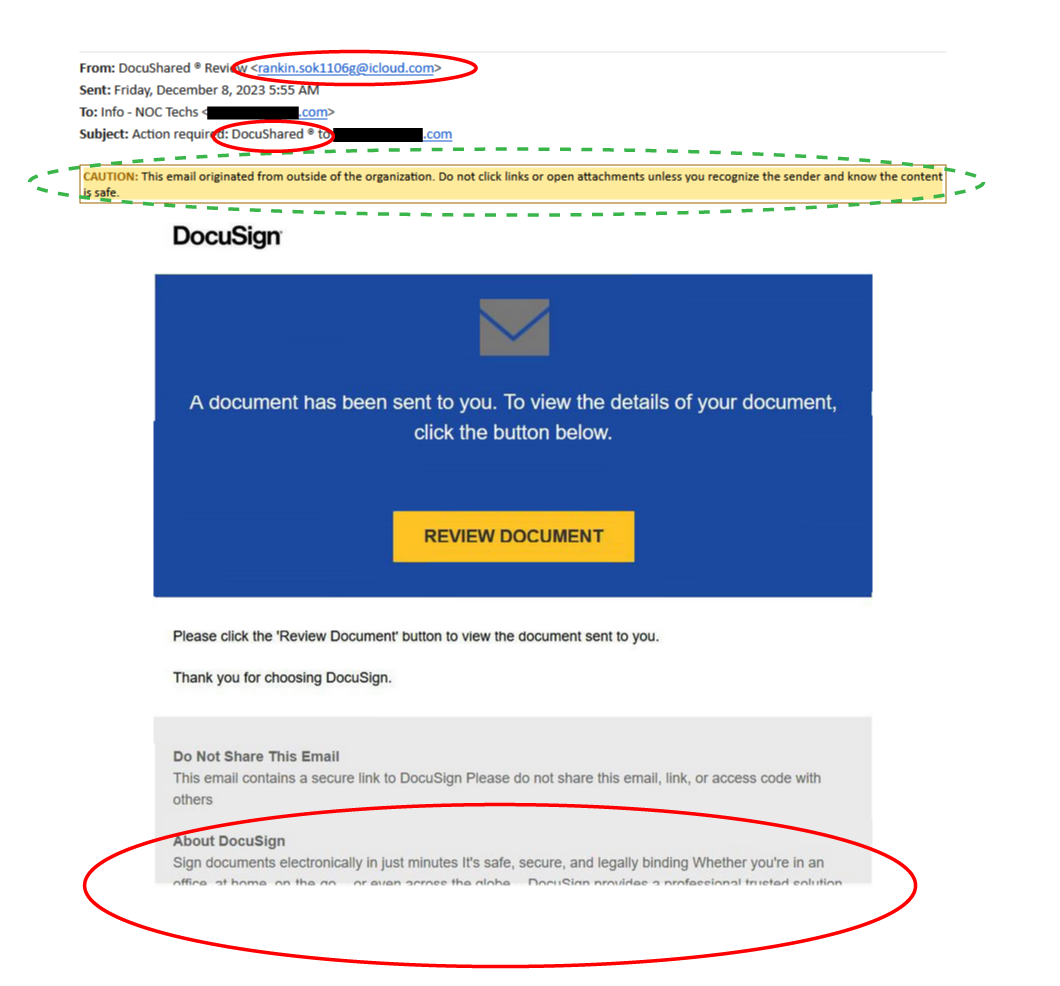
- Communication regarding an unsolicited service: If you are not expecting to provide your electronic signature for legitimate reasons, you should immediately disregard any such communications.
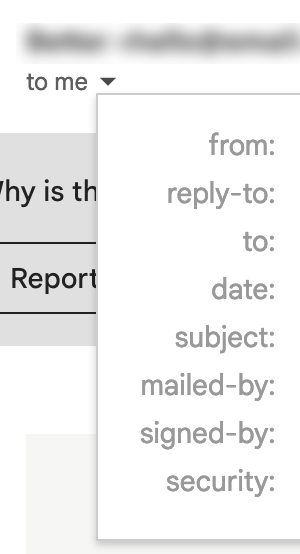
- Sender’s email address: Though many scammers conceal their identity by spoofing their sender name, a quick peek at the actual email address should reveal whether or not an email is legitimate. Communications from DocuSign should always end in @docusign.com or @docusign.net (or a regional equivalent). Any iCloud, Gmail, Yahoo, or other type of personal account indicates fraud. However beware spoofed email addresses. While dse_na4@docusign.net does end in the proper domain, make sure it is the actual sending address. (In Gmail, you can do this by clicking the little arrow next to the address for full information.)
- Information via image file. The entire body of this email is a PNG file. Though they may insert JPG or PNG files for visual flair, respectable organizations are not likely to send important information in an image file.
- No personally identifying information: Everything about this email is generic, since it is likely bcc’d to an anonymous list of potential victims. The scammer did not include any specific information in the email—such as the target’s name.
- Caution banner: Although most of us are now used to ignoring warning banners—this email is a perfect example of why we should not. The banner is intended to make us double-check the details of an email from an external origin—just to be sure.
- Inconsistent use of the DocuSign name: Although the term appears several times in the email details, “DocuShared” is actually a Xerox product.
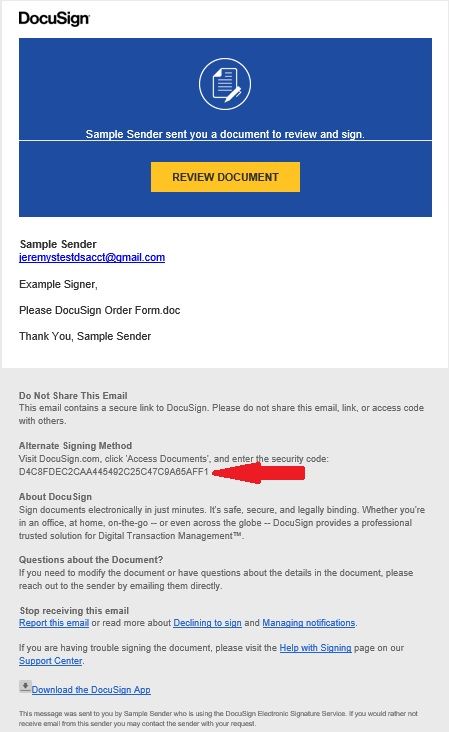
- Missing security details: Though casual users might not know to look for this security feature, DocuSign emails will always provide an alternative method to validate any requests for a signature. All DocuSign signature requests contain a unique security code that allows users to access their file directly from the official DocuSign website. This information has been intentionally cut off from the bottom of the image in our fraudulent email.
Suspicious subject lines and content
Although our example email did not use this particular tactic, DocuSign has previously reported that emails including this content are likely spam.
- MS Office 365
- Windows Defender purchased order
- Order successfully
- Complete with DocuSign: Bot Content (90).html
- Fire wall protection order successfully placed
In late 2023, DocuSign also reported a new phishing scam in which bad actors impersonate HR departments. Those scams include the following subject lines.
- New Employee Benefit and Compensation & Salary Increment for your Review
- New Benefit and Compensation
- HR Sent you a document
- EMPLOYEE BENEFIT POLICY
Incorrect branding
It's also worth noting that Docusign
changed their logo in April 2024. You can be sure that any genuine communication from the company will follow the new brand standards.

What should you do with a DocuSign scam email?
Once you have determined that the email in your inbox is not legitimate, take the following actions to protect yourself and others.
- Report the fraud to DocuSign. Fortunately, DocuSign is well aware of phishing scams and is working hard to combat fraud being sent in their name. Forward any fraudulent emails to spam@docusign.com. You can learn more about DocuSign phishing attacks and website spoofs in their white paper.
- Report fraud to the FTC. As the federal entity in charge of consumer protections, the FTC asks you to report this type of phishing scam through their dedicated Report Fraud website.
- Report phishing to your email service provider. Most major email providers (like Google and Microsoft) make it easy to report phishing. You should see a button in your inbox to Report as Spam/Phishing/Fraud.
- Block the sender.
- Permanently delete the email. Make sure to eliminate the email from your inbox and your trash can in order to eliminate the possibility of an accidental click in the future.
Did you bite? What to do if you fell for a DocuSign scam.
No, but... what if I clicked?
Unfortunately, this happens every day. (If it didn't work, cybercriminals wouldn't try.)
Time is now of the essence. Move quickly, to mitigate the damage caused by this fraud.
- If you paid a scammer through Western Union, MoneyGram, or a debit, credit, or gift card, you should immediately contact the financial institution that facilitated the payment and let them know that it was a fraudulent charge and ask them to reverse the payment or refund your money. If you sent cash through the USPS, you can attempt to intercept your package before the scammer receives it. If they receive the cash, or if you paid in cryptocurrency, you will probably not be able to recover your money.
- If a scammer has access to your personal information such as your social security number or identifying information, visit identitytheft.gov to report the theft and put together a plan to recover your identity.
- If you gave a scammer your username and password, or suspect that they have remote access to your phone or computer, run antimalware software on your computer immediately and seek professional help from a cybersecurity expert.
The
FTC maintains a helpful page of advice and resources for anyone that has fallen prey to a phishing scam and provides specific instructions for what to do in your particular dilemma. In many cases, you will have a better outcome if you respond as quickly as possible to the issue. Act quickly and seek professional assistance if you feel that the issue is beyond your ability to address.







