Is that PayPal Email a Scam?
by Jon Lober | NOC Technology
How to identify a fake PayPal email and what to do about it.
Updated January 26, 2024

As phishing becomes a part of our daily lives, we wanted to present our readers with some real-life examples of how phishing impacts real people and businesses every day.
Phishers have been testing the internet’s waters for years, and their skills have improved dramatically—as have their catches. Each service and resource that moves online represents an opportunity to land one more victim. Phishers keep trying out new lures, attempting to stay one step ahead of the tools and training of cybersecurity professionals.
NOC is reaching out to our community to ask for their own phishing stories, which we will share over the following weeks. Many stories will be anonymous, but we wanted to start with a recent personal story of a basic phishing attempt on one of our own staff’s personal email accounts.
Each of “Phishing Reports” will include a detailed description of the phishing attempt, the methods used (the lures), the result (the catch), and suggestions for how readers can detect or avoid such an attempt.
What is phishing, and why does it matter?
The FBI (Federal Bureau of Investigation) defines phishing as “the use of unsolicited email, text messages, and telephone calls purportedly from a legitimate company requesting personal, financial, and/or login credentials.”
Practically, this means that someone contacts you, pretends to be from a legitimate company, and tries to get you to share your personal information with them. Once they have enough personal information, they can use it to access your accounts to steal your money, blackmail you, or sell your information on the dark web.
In its 2022 Internet Crime Report, the FBI recognizes phishing as the most commonly reported type of cybercrime, with more than 300,000 reported attempts in 2022 resulting in a combined loss exceeding $50 million.
Though most phishing happens through email, the crime has many variants. Smishing refers to such an attempt via SMS text. Vishing or “voice phishing” happens over the phone or through voice message. Angler phishing happens through social media accounts.
“Spear phishing” uses a full suite of refined social engineering tools to imitate real individuals that could be known or trusted by the target. These attacks normally aim to steal sensitive information or large amounts of money.
Due to its complexity, spear phishing is often classified completely separately from run-of-the-mill phishing. One specific subset of spear phishing, known as Business Email Compromise (BEC) is estimated by the FBI to be the second-costliest type of cybercrime—even surpassing ransomware. In 2022 alone, the FBI reported an astounding $2.7 billion in collective losses to affected businesses.
When successful, BEC attacks have the unsettling potential to shut down small businesses through loss of reputation in the marketplace, downtime, and the gaping hole they leave in business finances.
In our “Phishing Reports,” we will share a diversity of attacks—both successful and unsuccessful—and keep you informed of how you can protect yourself and your business.
Now, on to the report.
Email Phishing: PayPal Fraud
In June 2023, one of our staff members received an email from “PP Support Team #9387” with the subject line: “Your Purchase E-Receipt. Your Invoice NoPRX7-Q8W3ER4C8B46813283555 of item.”
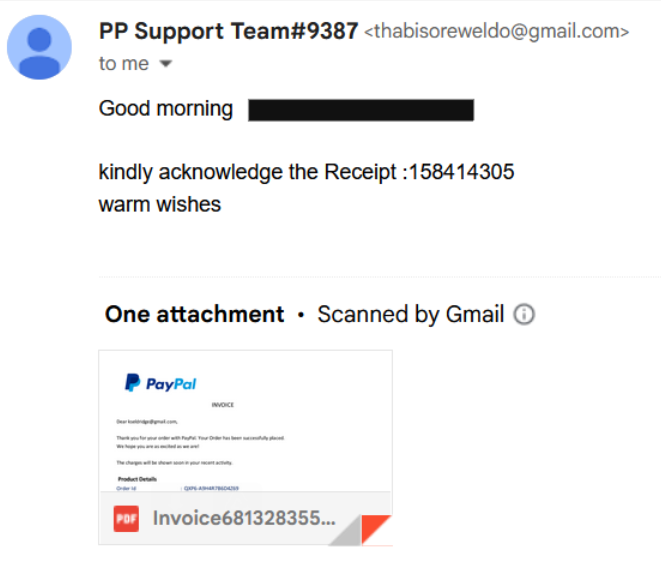
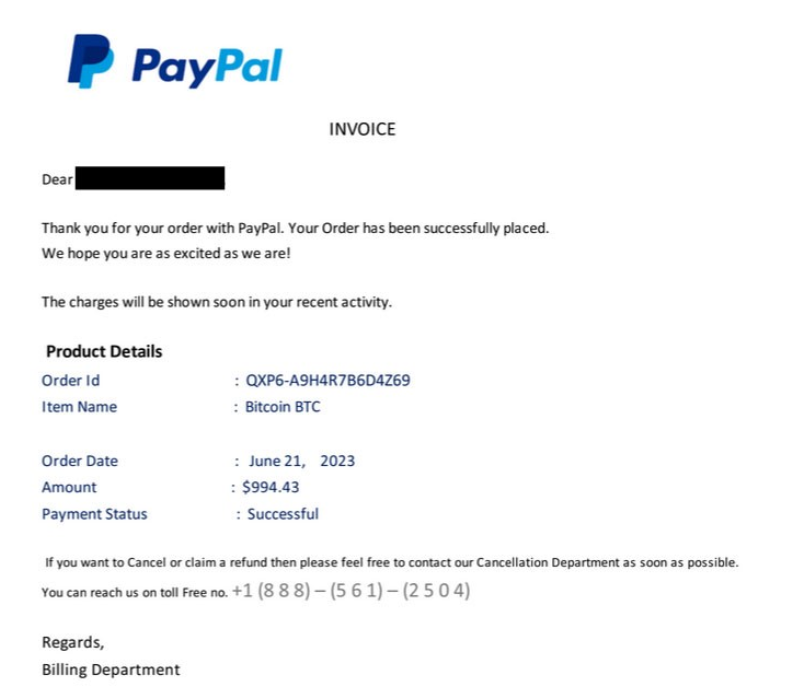
Attached to the main body of the email was a PDF invoice, purporting to be from PayPal. At first glance the invoice appeared legitimate and included PayPal’s official logo. It also referenced an order ID, an item name (Bitcoin BTC), a specific amount ($994.43), and a payment status. At the bottom of the invoice was a telephone number for the “Cancellation Department” for any desired recourse.
Phishing Lures: The Phisher’s Methods
In this common phishing scenario, the phisher did not reach too deeply into their tackle box—choosing instead to use a common set of lures. Although independently, each of these methods do not represent a terribly convincing scam, when they are combined, they could be enough to dupe an untrained or unsuspecting victim.
- Spoofed Email Sender: The sender seems legitimate—PP Support Team #9387
- Attached PDF Invoice: The subtle detail of using a trusted file format (like PDF) to send their primary details uses a veil of security to mask their intentions. Since the attachment did not contain any malware, Google indicated that the invoice was safe to open, adding an additional layer of apparent legitimacy.
- Name of a recognizable, trustworthy company: The PayPal name is synonymous with security and reliability. The scammer’s use of the PayPal name and logo plays directly to a potential victim’s inherent trust in the company.
- Abundant details: The scammer took their time to develop a convincing set of details in the fake invoice. Item name, order date, amount, payment status, and order ID are all fields that you would expect to find in such an invoice.
- No direct requests, pressure, or links: This is the most sophisticated method used by the scammer. At no point do they push for a response, request any information, or provide a compromised link—actions that could trigger red flags for wary recipients.
The scammer was hoping that the combination of these elements would convince the recipient to either call the number listed at the bottom of the invoice or respond via email. In either case, the scammer would have asked the recipient for their personal or financial information to “verify the account” or “start the refund process.” This information is the end goal of phishing.
Red Flags: How to recognize it as a scam.
Although the bad actors behind this attempted fraud did use several effective techniques, they also made some mistakes. In addition to their mistakes, most phishing emails have a dead giveaway right at the very beginning for those that care to look.
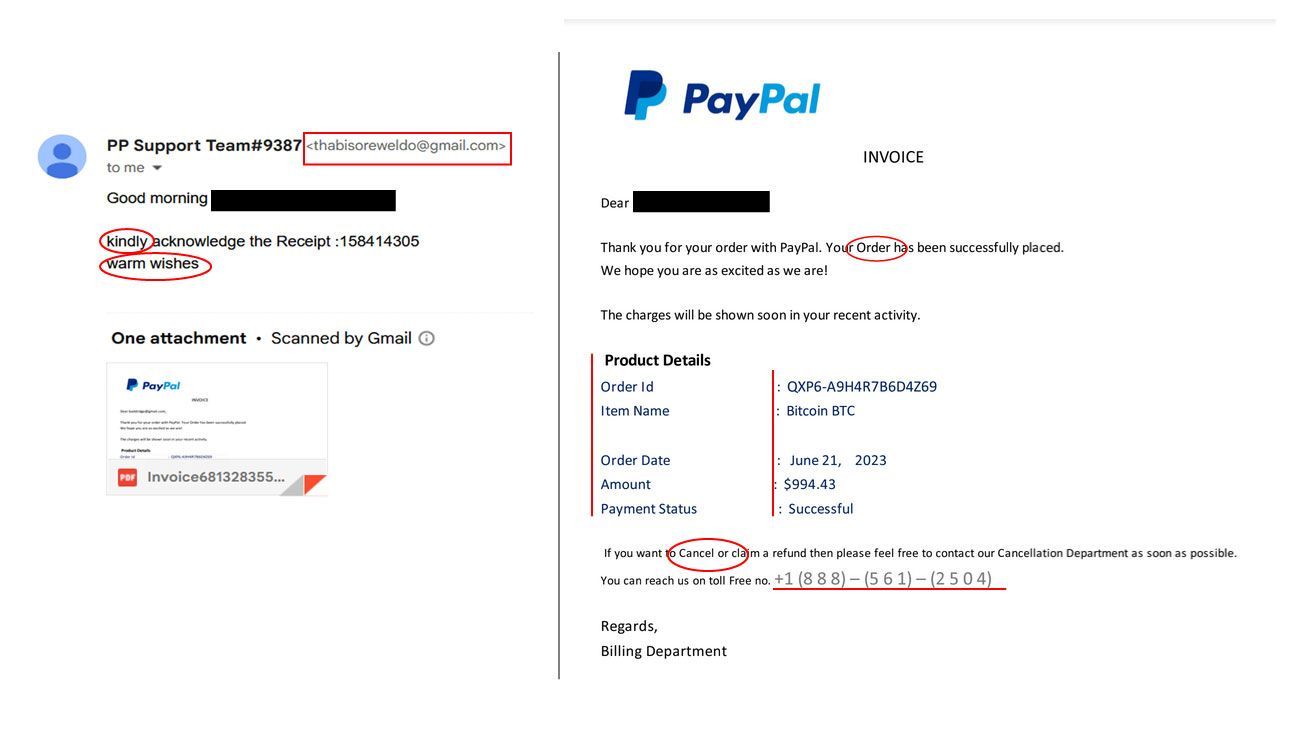
- Spoofed sender address: This should always be the first thing you check when you receive a suspicious email. The red rectangle in the image above shows that the sender is not using an official “@paypal.com” email address, but in fact an unrelated Gmail account. This is a plain indication that the email is not legitimate.
- Incorrect grammar: The red ovals in our image indicate several obvious capitalization, usage, or punctuation errors, which are unlikely to originate from a business with the level of resources possessed by a tech giant like PayPal.
- Inconsistent visual style: The red lines above demonstrate misalignment in columns and changes in text color, font, and size.
- Unusual verbiage: The word choice throughout the email is not formal and does not follow common English language conventions, making it feel a bit awkward.
- Unfamiliar content: Since the email recipient had never purchased cryptocurrency (from any source), this immediately raised their suspicions that something was wrong.
How to report a PayPal scam.
Once a user has identified a fake PayPal email, how should they proceed?
- Do not click any links in the email (very important)!
- Report the email to PayPal by forwarding the message to phishing@paypal.com
- Report the email to the authorities. The FTC and the FBI both maintain dedicated webpages for users to report this type of fraud.
- Report the email as phishing to your email provider.
- Block the sender.
- Permanently delete the email.
Although this example is somewhat sloppy, similar attempts are prevalent and often painfully effective. In May 2023, the FTC (Federal Trade Commission) issued an alert to consumers about PayPal-related phishing. Both the FTC and PayPal ask for affected consumers to forward such emails to them for analysis before blocking the sender and deleting the email from your inbox.
If you encounter such communication, never click any links, forward the email to the authorities, block the sender, and permanently delete the email.
Unfortunately, scammers are abusing far more than just PayPal. Read our other phishing reports to learn how to spot scams that spoof Geek Squad, Dicks Sporting Goods, QR codes, Microsoft 365, and others.







